Vulnerability and Update Management
One of the most important things that every organization needs to do is ensure that every computer, device, and application is consistently updated.
In addition to addressing bugs and adding new features, patches and updates are frequently used to remediate vulnerabilities. New vulnerabilities are found every day, presenting an unpredictable threat to organizations around the globe.
Small businesses, in particular, are at risk due to factors like often having less robust cybersecurity measures in place, limited IT staff, and using potentially outdated systems.
To understand this important topic, we need to take a close look at vulnerabilities and how they relate to patches and updates.
What are Vulnerabilities?
A vulnerability is any weakness in a digital system, process, or set of controls that can be exploited by an attacker.
Vulnerabilities can occur in both hardware and software, and the worldwide cybersecurity community constantly tries to identify them.
Attackers want to identify vulnerabilities present on target systems and exploit them to achieve various goals. These include gaining initial access to a system or network, gaining access to data that they shouldn’t be able to, escalating privileges on a system that they already have access to, or moving laterally across a network.
Defenders, on the other hand, want to prevent the damage that attackers can do by exploiting vulnerabilities. So cybersecurity practitioners on the defensive side want to identify vulnerabilities so that they can be remediated before they are exploited by an attacker. They also want to keep their networks free of vulnerabilities in order to protect the business infrastructure.
Vulnerabilities, Updates and Patching
Once a vulnerability is identified, the vendor typically rushes to produce a patch that will resolve the issue. For example, if a vulnerability in Windows is identified, Microsoft will produce a patch as quickly as possible. Sometimes, patches are released immediately and sometimes they are included with a larger update.
After a patch or update is released, it’s up to the customer to ensure that their software gets the patch or update. This is why the process needs to be managed.
Many times, vendors themselves identify vulnerabilities in their products and quietly work on a patch to resolve the vulnerability. They want the have the solution in hand before they announce the problem to the world. They test and release the patch before (or at the same time as) announcing the existence of the vulnerability.
New vulnerabilities are often discovered when vendors hire ethical hackers to perform penetration tests or open their products to a bug bounty program. We’ve seen cases where penetration tests identify several significant vulnerabilities in software, especially if the product hadn’t undergone significant testing in the past. It’s highly advantageous for software companies to discover vulnerabilities by hiring ethical hackers, rather than waiting for their applications to be exploited by bad actors in the wild.
Sometimes, the bad guys discover vulnerabilities before the good guys do. In this case, the vulnerability is known as a zero-day, and the attackers are often free to use and abuse it however they decide. Advanced groups of hackers called ‘Advanced Persistent Threats’ (APTs) and nation-state actors actively hoard zero-day vulnerabilities to use in their own engagements.
Once a vulnerability is discovered, it’s also important that it be identified and classified for the benefit of the world’s security. One of the most popular ways to do this is by using the Common Vulnerabilities and Exposures (CVE) system.
Common Vulnerabilities and Exposures (CVEs)
CVE stands for Common Vulnerabilities and Exposures, and it’s a system for identifying and cataloging publicly known vulnerabilities. You can learn more at the cve.mitre.org.
Each vulnerability is assigned a unique identifier (e.g., CVE-2025-12345) to make it easier for cybersecurity professionals to discuss and reference vulnerabilities consistently.
The CVE system is maintained by the MITRE Corporation, which is a not-for-profit organization backed by the US government. It offers the entire database available online for free.
Once a vulnerability has been publicly announced as a CVE, the entire cybersecurity community can learn about its existence and potentially, how to exploit it.
Many popular vulnerabilities have publicly available ‘Proof of Concept’ scripts, which can be used to easily exploit the vulnerability. In addition, the vulnerability may eventually be included in offensive cybersecurity tools such as Metasploit, which can offer a seamless experience from identifying the vulnerability to exploiting it. Metasploit goes much further; enabling researchers to perform thousands of attack types and stealthily move through a network.
From the perspective of the small business, the most important thing we need to understand is how to defend against vulnerabilities.
Defending Against Vulnerabilities
The most important thing that an organization can do to defend itself against known vulnerabilities, is to have a vulnerability, patch, and update management program in place.
What this means, is that someone at the organization needs to be in charge of ensuring every system is fully updated – including things like every piece of software, drivers, chipset software, and the operating system.
This person needs to be allocated an appropriate amount of time to complete the task – we estimate about 15-30 minutes per workstation or laptop, and at least 30-60 minutes per server. The point is that small business owners shouldn’t consider updates to be trivial, or automatic.
In addition, many find that the task is made far more manageable by using update or patch management software. As an IT service provider, we often use a type of software called a Remote Monitoring and Management (RMM). There are a lot of good ones out there.
Patch and update management is key, but organizations also need to think about defending against zero-day vulnerabilities, as well as attacks that don’t involve exploiting vulnerabilities (like phishing, or business email compromise). The first line of defense against these types of attacks is an Endpoint Detection and Response (EDR) software or Managed Detection and Response (MDR) service. We’ll learn more about EDR/MDR later in this course.
Vulnerabilities Becoming More Common
The number of CVEs (Common Vulnerabilities and Exposures) has seen a significant rise over time, and we expect this trend to continue as the world continues to embrace technology. The more tech we use, the more vulnerabilities we can expect to find.
The last five years have seen an annual growth rate of around 14%, and we’ve seen around a 30% growth rate from 2023 to 2024 alone (Intelligent CISO, 2024).
So, at least for the foreseeable future, vulnerability management will become increasingly important for small businesses to contend with.
Aren’t Updates Automatic?
There is often a bit of confusion about updates – aren’t they automatic?
After all, we’ve all seen those popups in the bottom corner of our screen telling us to update, or been forced to close and open our browser so that it can update. Most of us have had to wait much longer than we’d like for an update to complete so that we can get back to work.
The reality is that only some types of software tend to keep themselves well updated, while other types of software don’t.
For example, operating systems like Windows and macOS, tend to do a good job of integrating patching and updating into their daily functionality. However, most other applications require user interaction to be able to detect that a patch or update is available. This is actually a good thing; imagine if all of our applications were going online and looking for updates every day? That would use a lot of system resources and present a potential security risk by itself.
So most applications are only programmed to look for updates when they are started. That’s why you’re likely to get an update prompt if you’re using an application that you haven’t in a while.
What this means is that, even for applications that do the work of going out and looking for updates (so you don’t have to), they only do this when they’re run by the user. Other applications may even require you to manually look for updates, but this is rare.
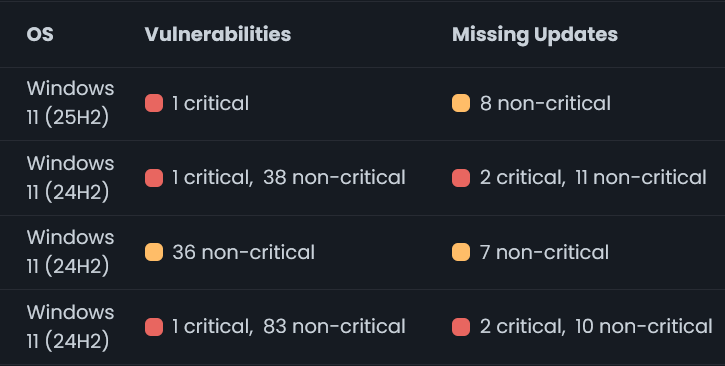
The result is that most computers online today, have significant vulnerabilities that can potentially be exploited. We know this, because we commonly find numerous vulnerabilities on client machines during the onboarding process. It’s common for us to find several critical vulnerabilities along with a handful of high, low, and medium.
Shameless Plug: The Security Essentials
The Security Essentials is a set of curated cybersecurity services that we offer. For just $25 per month (as of Jan 2025), it includes our Perfect Patching and Update Management service, along with Fully-Managed Detection and Response backed by a 24/7, world-class Security Operations Center – and a bunch of extras to boot.
As part of the Security Essentials, we track new vulnerabilities as they emerge, along with managing patches and updates for hundreds of the most common applications.
Security Essentials is designed to provide true enterprise-grade protection against both known and zero-day vulnerabilities.
